Exploring Cyber Security: Adapting to AI's Impact on Digital Safety
In this blog series, we delve into the evolving landscape of cyber security, focusing on critical topics like the influence of generative AI and the challenges of application security. Stay informed and learn how to navigate these new frontiers to protect your digital assets effectively.
11/8/20244 min read
The Changing Landscape of Cybersecurity in the Era of Gen AI
The arrival of generative artificial intelligence (Gen AI) is transforming numerous sectors, with cybersecurity standing out as one of the most critically impacted. The technology brings forth both unprecedented opportunities and formidable challenges. This article explores how Gen AI is redefining the cybersecurity landscape, enhancing defence capabilities while also creating new threats, and outlines key considerations for CISOs and senior management to address these emerging challenges effectively.
The Evolution of Cyber Threats
Traditionally, cybersecurity threats have been relatively static, with malicious actors relying on a known set of tactics, techniques, and procedures (TTPs). However, the rise of Gen AI has catalysed a shift towards more sophisticated and adaptive threats. Unlike conventional AI, which primarily focuses on pattern recognition and anomaly detection, Gen AI can autonomously generate content, simulate human behaviours, and even create new malware strains.
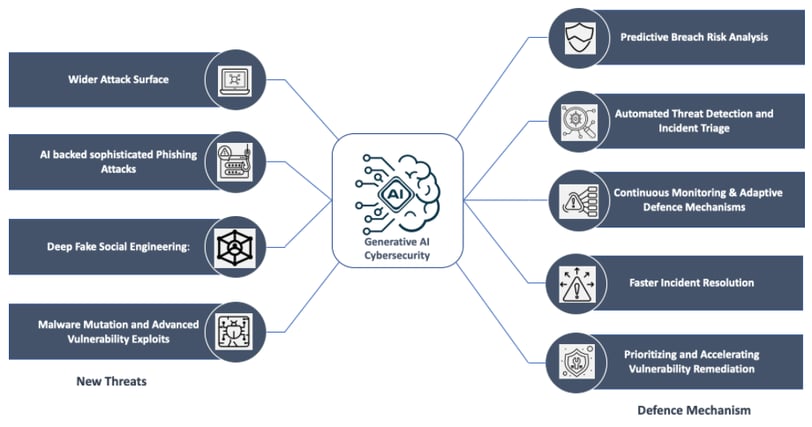
Generative AI is a game-changer in the cybersecurity ecosystem due to its dual nature of posing new threats while also offering significant enhancements to defence mechanisms.
As the landscape of cybersecurity is undergoing significant transformation in the era of Gen-AI. The rapid advancement of AI technologies, including those that generate text, images, and code, is reshaping both the threat landscape and the defence mechanisms available to cybersecurity professionals. Here’s how:
1. Enhanced Threat Detection and Response
• AI-Driven Security Solutions: Gen AI models can analyse vast amounts of data to identify patterns and anomalies that might indicate a cyber threat. This enhances the ability to detect and respond to attacks in real-time, reducing the potential damage.
• Automation and Predictive Analytics: By leveraging AI, cybersecurity tools can predict potential attack vectors and automate responses to mitigate risks before they materialise.
2. New Attack Vectors
• AI-Powered Cyber Attacks: Cybercriminals are using Gen AI to craft more sophisticated phishing attacks, malware, and social engineering tactics. AI can generate highly convincing fake content, making it harder for individuals and systems to distinguish between legitimate and malicious communications.
• Automated Hacking Tools: AI is being used to develop automated tools that can identify and exploit vulnerabilities in systems, potentially leading to an increase in the scale and speed of attacks.
3. Challenges in Authentication and Identity Management
• Deepfakes and Voice Cloning: Gen AI can create realistic deepfake videos and clone voices, challenging traditional authentication methods like facial recognition and voice verification. This raises the stakes for securing identity and access management systems.
• Spoofing and Impersonation: The ability of Gen AI to mimic individuals or create synthetic identities makes it easier for attackers to bypass security measures through impersonation.
4. Data Privacy and Protection
• AI-Generated Content and Data Privacy: The generation of synthetic data by AI, while useful for preserving privacy, also introduces new challenges in terms of data protection. Ensuring that AI-generated content does not inadvertently leak sensitive information is critical.
• Regulatory Compliance: The rise of Gen AI necessitates new regulatory frameworks to govern the use of AI in cybersecurity, ensuring that it is used responsibly and that data privacy is maintained.
5. Adversarial AI
• AI vs. AI: As defenders use AI to protect systems, attackers are also using AI to find and exploit weaknesses in these AI-driven defences. This creates a new battleground where AI algorithms are pitted against each other in a continuous cycle of attack and defence.
• Adversarial Attacks: Attackers may use techniques like adversarial machine learning to fool AI models, causing them to make incorrect decisions, such as misclassifying malicious activity as benign.
6. AI Ethics and Bias in Cybersecurity
• Bias in AI Models: AI systems are only as good as the data they are trained on. If the training data is biased, AI-driven security tools may be less effective in certain contexts, leading to vulnerabilities.
• Ethical Considerations: The use of AI in cybersecurity raises ethical issues, particularly around surveillance, privacy, and the potential for AI to be used in ways that infringe on civil liberties.
7. Skill Gaps and Workforce Evolution
• Need for AI Expertise: The integration of AI into cybersecurity creates a demand for professionals with expertise in both AI and cybersecurity. This requires upskilling the current workforce and developing new educational programs.
• Changing Roles: As AI automates more routine tasks, cybersecurity professionals may shift towards more strategic roles, focusing on areas like AI oversight, ethical considerations, and the development of advanced threat detection strategies.
8. Global Cybersecurity Landscape
• Nation-State Actors and AI: Countries are increasingly leveraging AI in their cyber operations, both for defence and offense. This has implications for national security and the global balance of cyber power.
• Collaboration and Information Sharing: The complexity of AI-driven cyber threats necessitates greater collaboration between governments, private sectors, and international organisations to share threat intelligence and develop collective defences.
CISO and Senior Management’s Key Considerations
The role of CISOs (Chief Information Security Officers) is evolving significantly in the era of Generative AI. As organisations navigate this transformative period, it is crucial for security leaders to understand and adapt to the unique challenges and opportunities presented by Gen AI. Key considerations for CISOs and senior managers include:
▪ Strategic Alignment: Cybersecurity must align with overall business objectives, integrating AI to enhance security and drive innovation.
▪ Adapting to AI-Driven Threats: CISOs need proactive threat management, utilising AI for threat intelligence, automated detection, and adversarial AI preparedness.
▪ Ethical AI Usage: Ensuring AI systems are fair, unbiased, and privacy-compliant, with transparency and accountability in AI decision-making.
▪ Workforce Transformation: Investing in upskilling cybersecurity teams for AI, fostering cross-functional collaboration, and promoting human-AI collaboration.
▪ Continuous Monitoring: Adopting adaptive security frameworks, continuously evaluating AI models, and utilising real-time analytics.
▪ Regulatory Compliance: Staying informed on evolving AI and cybersecurity regulations, ensuring compliance with data protection laws, and understanding legal risks.
▪ Investment in Emerging Technologies: Exploring next-gen AI-driven security solutions, considering AI-powered SOCs, and partnering with AI innovators.
▪ Culture of Security and Innovation: Promoting a security-conscious culture, encouraging innovation, and leading by example in communicating the importance of cybersecurity in the AI era.
Conclusion: Navigating the Gen AI Cybersecurity Landscape
Generative AI is reshaping cybersecurity, offering powerful tools for defence while also enabling more sophisticated attacks. For CISOs and senior managers, this dual nature of Gen AI demands a strategic, proactive approach. Aligning AI-driven security with business goals, ensuring ethical use, and continuously adapting to new threats are essential. Success in this evolving landscape requires leveraging AI to strengthen defences while staying vigilant against its misuse by cybercriminals. In this new battleground, integrating AI into cybersecurity is not just an advantage—it's a necessity for future protection.
